FortiOS 5.0 onwards, changing the switch mode to interface mode in FortiGate firewall devices is different from earlier versions. I experienced this situation and could not find the option to change the switch to interface mode at the usual place. Even though I converted the mode in CLI, there is a way in GUI also.
If you suddenly started using the latest Fortigate versions like 7.2, 7.x and 6.x from the earlier versions, the GUI and interface mode options will look different. This guide will be useful to convert the interface mode in Fortiagete.
The straightforward option used to available in the web interface under settings of network ports in earlier FortiOS, like 4.0 and 3.0. But we can’t find the same option on the latest OS versions. This change is similar to the feature removal of third-party DDNS providers in the latest Fortigate OS.

Fortigate is one of the best network security hardware devices which can do a lot of things in the firewall, network security, internet proxy, VPN and more. You can find more information about their products, features, and technical details here at the official site.
Change Switch Mode to Interface Mode in Fortigate FortiOS 7.2, 7.x & 6.x
From the FortiOS 6.0 and later versions, we can remove the network ports from the default hardware switch easily. Once these ports are removed, they become Interface mode. This is the simple method to change switch mode to interface mode in Fortigate that allows different settings & policies separately.
To do that, right-click (or double-click) the hardware switch and remove the ports you want to convert to interface mode.
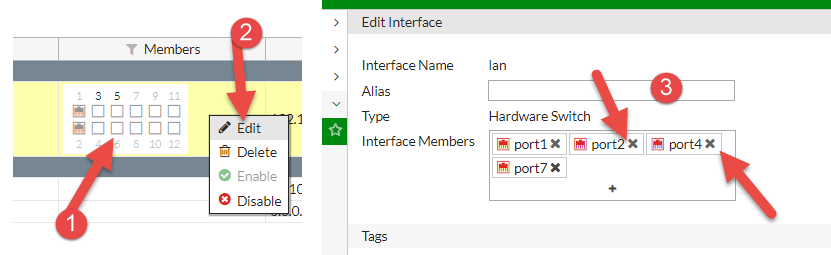
There should be a minimum of one port part of the hardware switch. We can’t remove all ports. Also, in this way, you can’t delete the entire hardware switch.
If you need to delete the entire hardware switch and make all ports to interface mode, follow the below steps.
Three steps are involved in this process.
- Complete the prerequisites.
- Change the mode from Switch to Interface.
- Configure the network and allow access to a particular network port.
1) Prerequisites to change the mode
By default, a brand new Fortigate Firewall comes in switch mode, default policy to allow Internet access, and DHCP to provide IP addresses. Even if you do a factory reset of an existing device, it will revert back to these settings only.
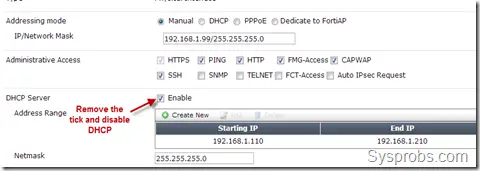
You must disable the DHCP service on the FortiGate device and remove any policies attached to the hardware switch interface.
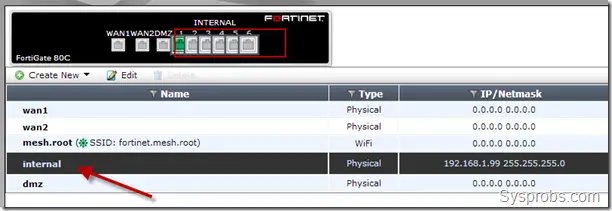
Here is a Fortigate device 80C which is in switch mode. All interfaces are combined together as a single ‘internal’ interface. In this case, we can’t have different settings (IPs, policies, etc.) for every LAN port in this device.
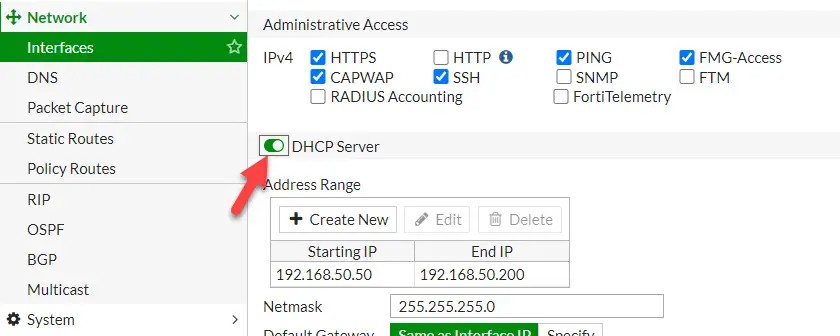
a) To remove DHCP, double click on the ‘internal’ and press edit. Deselect the checkbox of the DHCP server as shown below.
In FortiOS 6.x, it may look like the below.
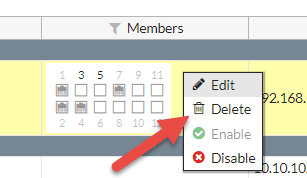
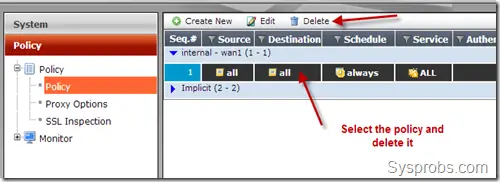
b) Remove any policies which are related to the ‘internal’ port (or the hardware switch), and normally you will find only one policy.
With the above two steps, now we are ready to change the mode.
Once DHCP and Policy are removed, you will get the option to delete the default hardware switch as shown below. Deleting the hardware switch/zone will convert all ports to Interface mode.
2) Changing from Switch mode to interface mode (in CLI)
In the older version of FortiOS or if you want to proceed with these steps by CLI/Telnet, here are the steps.
Use a serial cable and any telnet client software for this purpose. If you like to use a built-in telnet client of Windows check this guide.
Login with the default credentials, the username is admin and no password.
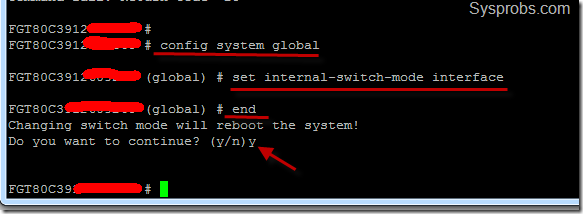
Type the following command,
config system global set internal-switch-mode interface end
Once the device is rebooted, it will not have any network settings. Therefore, we must configure an IP address and allow access (HTTP or HTTPS) to a particular network port that can be accessed through a network cable and web browser later.
Interface Mode in Fortigate FortiOS 5 and 5.2 in GUI/Web (Older versions)
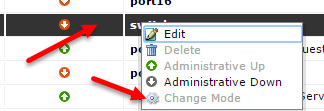
Once you have completed the prerequisites to change the mode, you can go to System->Network->Interfaces, then right-click on the internal interface to change mode. The option will appear disabled if still some policies and DHCP services are active on these ports.
Even after you changed the mode through CLI or GUI web interface and rebooted the device, you need to configure the next step by command-line interface only.
Follow the below step 3 to assign IP and allow specific access.
3) Configure the network and allow access to a network port
Earlier we changed the switch port to interface mode. Now the device will have n number of individual network ports that can have different settings and policies. After changing the mode, these ports will not have any settings including the management IP address. Use the same CLI to configure IP and allow HTTP or HTTPS access to a particular network port.
The below example shows how to allow HTTP and HTTPS access to a particular port and assign 192.168.1.100 IP with a subnet mask.
config system interface
edit <interface_name>
set allowaccess http https
set ip 192.168.1.100 255.255.255.0
end
Note: The latest Fortigate models have a separate network management port to access the device. This port is usually not part of the hardware switch. You do not need to worry about assigning IP and allowing access through Telnet if you have access to the Fortigate device via the management network port.
By the above steps, you should be able to change your Fortigate device from switch mode to interface mode in FortiOS 7.x and 6.x with CLI and GUI. This will enable you to have separate settings and configurations for every network port.





Hi,
Thankyou for the helpful info. I have another question. After changing to interface mode, the ports will have names like port1,2 etc. How can we change them back to WAN1, WAN2, internal etc for easier management?
Thanks again.
@Vin
WAN ports remain WAN1,WAN2..etc.
You need to set Alias for other ports to manage.
Thanks so much for posting the helpful info.
Hi, thanks for your info. I’ve seen that it’s also possible to delete the hardware switch in the interfaces overview. After deleting all correspoding policies, you can do it this way. I’ve checked this on my two Fortigate 100D, operating as a HA Cluster. Regards Chris
You can change mode of the interface by
Going into System->Network->Interfaces
Right Click on the Internal Interface then you will see the “Change Mode” options usually it will be disabled as you have to remove the DHCP and POLICY settings as you have described above
I had a problem were internal was in used, I couldn’t figure out where until i found this helpful command:
# diagnose sys checkused sys.interface.name internal
entry used by table system.dns-server:name ‘internal’
then I removed it from the dns-server:
# config system dns-server
(dns-server) # purge
This operation will clear all table!
Do you want to continue? (y/n)y
end
Hope it helps someone…
I was not able to change to interface mode on one 60D until I found out that NTP server was enabled on internal. My approach to find it was: “ssh admin@my_fortigate show | grep -3 internal”
The diag command would have been better, so thanks for the tip!
Thanks so much for that tip, I was starting to get annoyed because I was positive there was no policies called out for the internal interface
Is it possible to configure 2 ports [outside of the WANs] for 2 web connections with fail over or load balancing between them?
Thanks
David
Based on my knowledge, there is no difference between Internal and WAN ports. You can configure internal ports to connect to internet and configure policies. It will work fine.
Thanks for the article… very useful!
I have a 90D with 16 total ports. The product specs tell me that only 2 are provisioned for WAN. Is it possible to configure an additional 2 internal ports to act as WAN ports and add them to a load balancing group?
Thanks again!
Yes, you can add internal ports also.
hi
i did the command but is showing as
internal is in use
return code 23
very helpful… thanks..
I have a Fortigate 100D.
I was really surprised to find that the “hardware switch” in fact works as a hub broadcasting all unicast traffic on all the member physical ports.
Could somebody please enlighten me why this is and how to change it to actual switching.
THank you
martin3 (at) gmail . com
If I changed to Interface mode, can DHCP still be enable on those individual ports?
Christian — yes, DHCP is supported individually on each port, as they break out the same as your WAN1, WAN2, INTERNAL (which goes away) into port1, port2…port16 (or however many ports your unit has).
You can set up a DHCP server on each of these.
(same as you can on a VLAN interface, as well).